Firewall Management Tools in Linux
Table of contents
There are different tools to manage firewalls in various Linux distributions
iptables - iptables is a network filtering tool for Linux that allows or blocks network traffic based on predefined rules. Watching out for connections that attempt to establish themselves on a system or server, iptables analyses its internal rules to accept or reject the traffic based on a target.
firewalld - Firewalld is a Linux firewall control tool - an application that provides a custom server firewall, as well as a D-Bus interface and a full collection of firewall rules for managing inbound and outbound traffic across endpoints.
ufw(uncomplicated firewall) - Uncomplicated Firewall is a command-line application that attempts to create rules within iptables in Debian-based Linux distributions. Setting up firewall rules with ufw is a handy solution that does not compromise the system's security considering that ufw has less technical logic than iptables.
SETTING UP FIREWALL RULES USING IPTABLES
The function of iptables is for packet filtering. The packet filtering mechanism is organised into three different kinds of structures - tables, chains, and targets.
Tables allow you to process packets in a certain order. Tables are classified into four categories - filter, raw, mangles, and nat.
Chains - Each table has chains linked to it, and these chains allow you to inspect traffic at various places. To filter traffic, add rules to the tables. And if these conditions are met, you can then specify the target.
Chains in iptables
Input - monitors incoming traffic.
Output - monitors outgoing traffic.
Forward - through the router, moves from one endpoint to another.
Also to filter traffic by adding rules to the tables. And if these rules are met, you define the target.
Target - target defines what would happen to the traffic by allowing the system to either accept, reject or drop the packet.
WORKING WITH IPTABLES
To check if iptables is installed
For rpm-based systems
$ rpm -qa | grep iptables
If not installed, install
$ sudo yum install iptables-services
Start and enable the service
$ systemctl start iptable-services
$ systemctl enable iptables-services
To check iptables rules
$ iptables -L
To flush/delete all rules
$ iptables -f
For Debian-based systems
$ apt list | grep iptables
$ sudo apt install iptables -y
Note: For Debian-based distributions, iptables, firewalld and ufw do not run as a service. Hence, you do not need systemd utilities to either start, stop, enable or disable firewall settings. These tools are used as a standalone tools just like every other command-line tool in Linux.
- To drop all traffic coming from a specific IP - 192.162.20.20
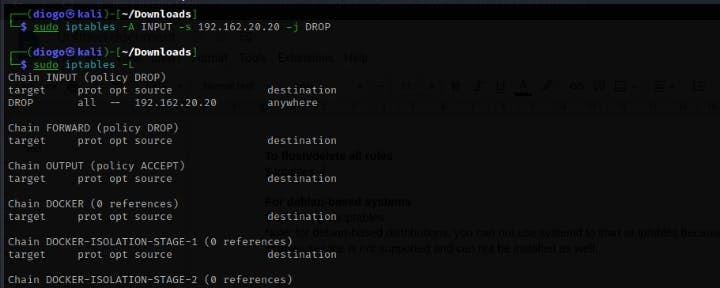
$ iptables -A INPUT -s 192.162.20.20 -j DROP
Where iptables is the command, -A is append (add traffic rules), INPUT is the chain (for inbound traffic rules), -s 192.162.20.20 the source IP address, -j is to check the target is met and if so, DROP to block the incoming traffic.
To Cross-check the added IP rule
$ sudo iptables -L
- To drop all inbound traffic from a range of IPs
To do this, specify the subnet mask to cover all the IPs coming in within the range of 32 bits.
$ sudo iptables -A INPUT -s 192.162.20.20/32 -j DROP
- To list the iptables by adding line numbers to the list. If you want to remove or reference a rule, you only need to supply the rule number rather than the whole row or command.
$ sudo iptables -L --List-numbers
- Delete a specific rule by number
$ sudo iptables -D INPUT 1
- To block a specific protocol eg ICMP
$ sudo iptables -A INPUT -p icmp -j REJECT
- To block a specific port for eg HTTP port 80
$ iptables -A INPUT -p tcp --dport 80 -j DROP
Where -p tcp is used to define the protocol, --dport 80 is used to define the port.
- To block a network interface
$ iptables -A INPUT -i enps03 -s 192.162.20.20 -j DROP
- To drop all outbound traffic for instance traffic going to www.amazon.com
First of all, find the IP address of www.amazon.com
$ host -t a www.amazon.com - find IP address
Secondly, set the outbound traffic rules
$ iptables -A OUTPUT -d 30.34.50.96 -j DROP
Where OUTPUT is to specify an outgoing traffic and -d 30.34.50.96 is the destination and its IP address
- To drop all incoming traffic except SSH
First to do is to accept traffic from SSH before dropping other traffic
$ iptables -A INPUT -p tcp --dport 22 -j ACCEPT
$ iptables -p INPUT DROP
- To save a rule and make the rule remain effective even after system reboot
$ iptables-save <rule number>
- To save all rules
$ iptables-save