Linux User Environment and Configurations
The obligation to protect the Linux operating system, its configurations, and its contents from faulty configurations and illegal access to certain activities, as they relate to its users and the business activities of enhancing the security of Linux Operating system and its services.
Security includes any sort of damage prevention, as well as a systematic effort to secure the entire system, including both software and hardware components, as well as the data it processes, uses, and stores, against loss, destruction, and unauthorized access.
Security strengthening refers to the elements and protocols that make the Linux system exceedingly harder to access, by unauthorized parties.
Security Implementation for Linux
There are different tools and software, manual configurations and automated methods that can be adopted to secure the Linux OS, Define user accounts and their privileges, secure the file systems, configuration files, servers, system access, and the system networks for inbound and outbound traffic rules.
User Environment and Configurations
- user files and configurations
The user configuration files are located in the /etc folder together with other system configuration files that dictate how the systems and applications can function. A passwd file under the /etc folder contains all the users starting from the root user username is also root, a password is X(encrypted), user ID is 0, the group ID is also 0, user information is root, Home directory for the root user is also root and the root shell environment as /usr/bin/zsh. This also applies uniquely to all users. To view the user's $ cat /etc/passwd
- Group files and configurations
Located in the /etc/group folder, this file contains details about different user groups in the OS. Once a user is created, ideally, a group should be defined where such a user can belong. Else the system automatically assigns that user to a group and this is an unhealthy user/group practice. For the root account, the group name is root, the password is X (encrypted) and the group ID is 0. To find out how many user groups are there in your OS
$ wc -l /etc/group.
- User password security
The /etc/shadow file is a file that stores the user's password in an encrypted format also with other details about that particular user such as the username, the last password change, and the number of days a user's password could last before the change. For security best practices, it is safe to limit the maximum number of days a user password could last before change according to the organization's password policy, usually between 2-6 months.
User Activities - Logs and Monitoring
With several users accessing the system/server, it is important to monitor each user's activities to know what they are doing, when they log in, how long they stayed, their login location etc. Through logs, evidence of each user's activity is obtainable and audited to validate such activity.
System user logs and monitoring tools
$ /var/log/messages - monitors user activities as well as all the messages relating to the system.
$ /var/log/secure - monitors user activities as well as their failures.
$ last - gives the history of all logged users. $ last <username> gives login information of a specific user.
$ sudo lastb - used to view all bad login attempts.
$ who or $ w - used to view the user currently logged in.
Project 1
- SETTING SECURITY PARAMETERS FOR USER ACCOUNT PASSWORD
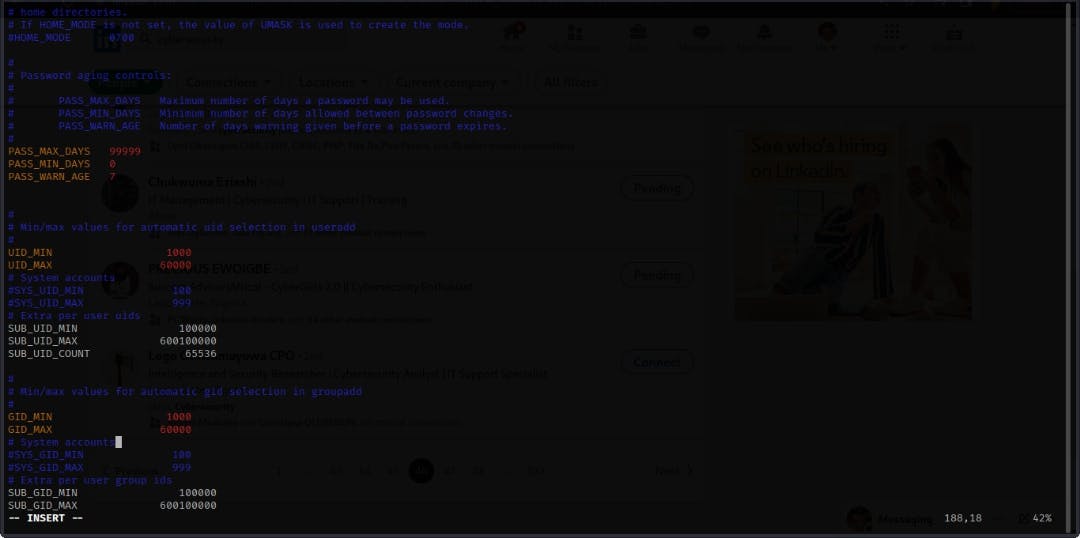
From the /etc/login.the def configuration file, you can specify the password length, the minimum and maximum number of days a user password can last, the password expiry date and warning days. Through this default configuration, each time a user is created, these password parameter values are automatically predefined for that user and other existing users.
Other configurations in this file:
UserID default configuration
GroupID default configurations
SystemID default configurations
Password encryption method
Note: All these configurations are subject to change based on the organisation's policy and parameters.
To set this default parameter, edit the login.def file
$ vim /etc/login.def
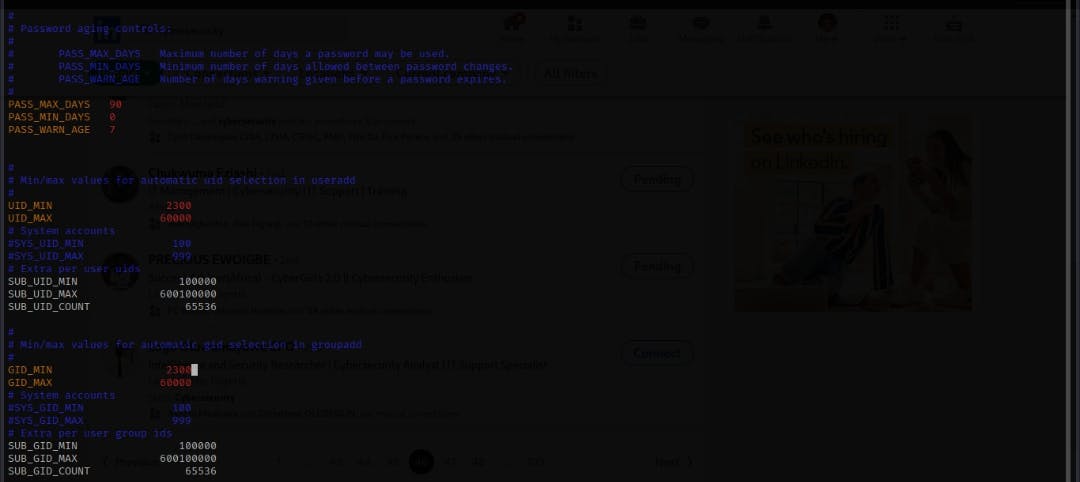
Change the maximum number of days to 90
Change the minimum number of user IDs to 2300
Change the maximum number of group IDs to 2300
Project 2
- Create 3 new user accounts, assign a password to each of them, put them in one user group, modify the expiry date of the users to 2023/07/01, set the minimum, their maximum days of password change to 30-35 respectively and their warning days to 28 days and define their password policy.
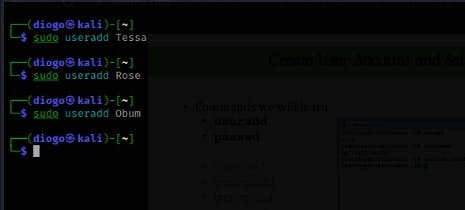
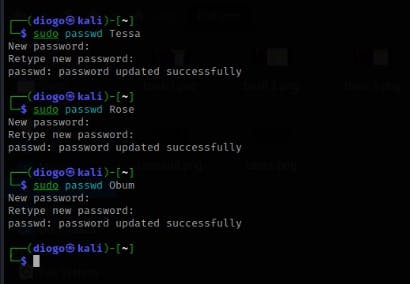
Creating users with the names Tessa, Rose, Obum
$ sudo useradd <username>
Adding passwords to existing users
$ sudo passwd <username>
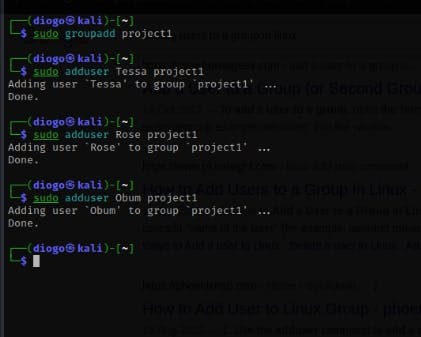
Create a group called project1 and add 3 users to the group
$ sudo groupadd <group name>
$ sudo adduser <username> <group name>
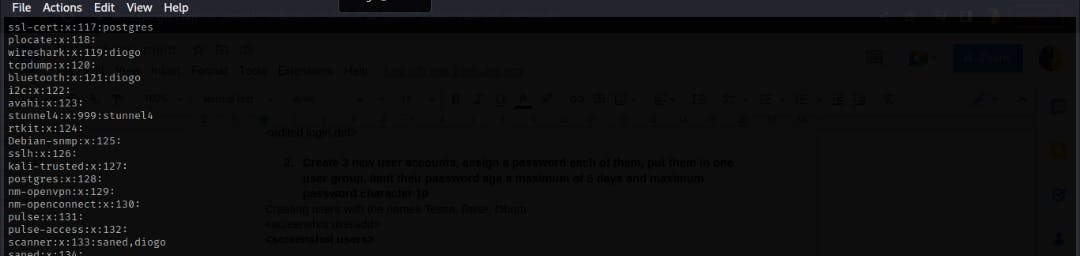
To view the group file
$ sudo /etc/group
User Modification
User modification is concerned with adjusting settings for users, specifically when it has nothing to do with their credentials. A user account can be set to lock, become inactive, be removed, or expire on a specific date via user modification. More of the flags that can be used for user customization can be found in the $ man usermod
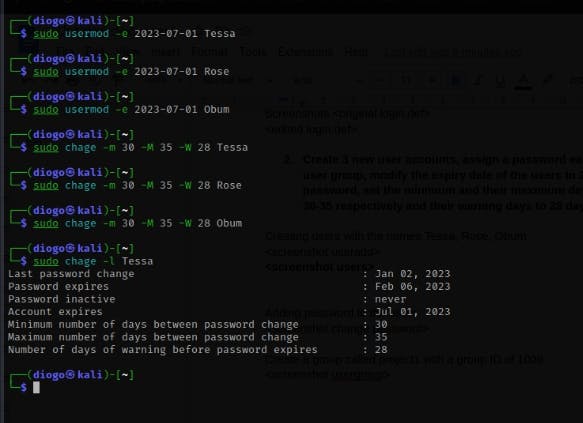
$ sudo usermod -e 2023-07-01 Tessa
Where usermod is the command, -e is a flag set to expire, 2023-07-01 is set in the format yyyy-mm-dd and Tessa is the name of the user.
With the $ chage command, other user account parameters around password expiry, warning days, and minimum and maximum number of days for password change are set.
$ sudo chage -m 30 -M 35 -W 28 Tessa
Where chage is the command, -m is to set minimum days for password change to 30, -M is to set maximum days for the password change to 35, -W is to set warning days at 28 and Tessa is the user account being modified.
Now, check user parameters and configurations with the -l flag to show the change information about the account.
$ sudo chage -l Tessa